June
2016
HYDROCARBON
ENGINEERING
53
work order sign-offs and visual inspections, adding
labour time and decreasing efficiency. With the mobile
worker, these operations can be completed
instantaneously at the job site using digitalised forms
and work orders on an intrinsically safe phone or tablet,
greatly enhancing wrench time. One recent example is a
refinery that averaged three hours to process a single
work order with all required sign-offs. Connecting the
workforce to an online collaborative environment across
the wireless infrastructure provided workers with
immediate access to online resources and forms,
reducing a three hour task to an average of 20 minutes.
Wireless is quickly becoming the technology of
choice for a number of customers because a single
wireless infrastructure delivers the most use cases
without the need for multiple parallel networks. The
number of projects is greatly increasing, much to the
satisfaction of early adopters, who are now
implementing large scale deployments.
Survey and deployment costs were previously seen
as barriers, but, after working with customers, an
organisation’s services develop cost effective and safe
methods that optimise surveys, lower deployment costs
and ensure pervasive cover in highly metallic and
hazardous environments.
Predictive automation and processes
In the plant, sensor and edge connectivity are essential
to achieving the maximum value out of automation. The
more that is connected, the better and richer the data
set that can be leveraged for correlation and to make
decisions. Through big data, fog or edge compute,
analytics and cloud-based services, sensors are able to
provide real time information on measures such as
temperature, vibration, pressure, flow and current.
Combining this with statistical models provides
predictive methods for the maintenance of equipment
and the streamlining of processes.
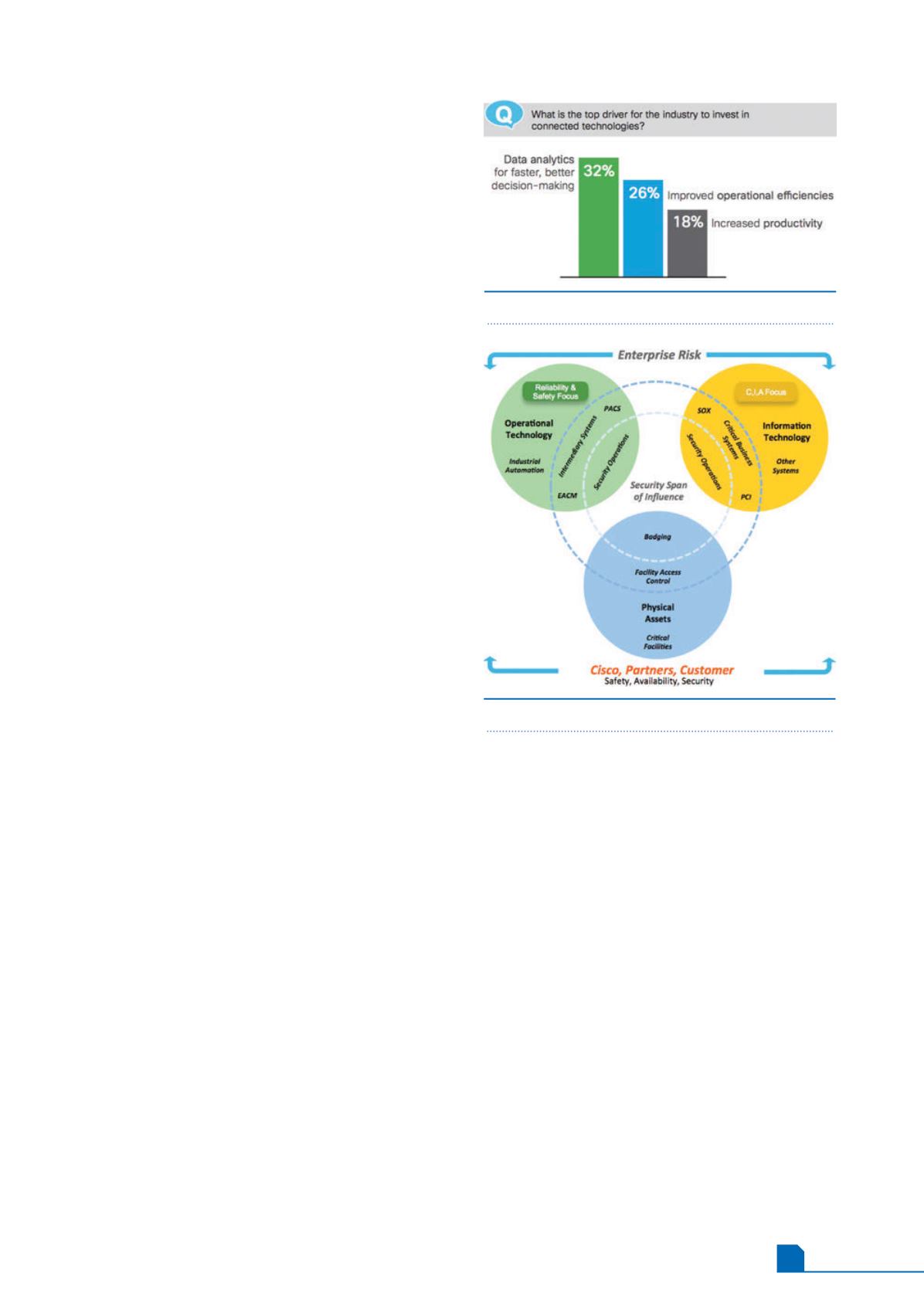
In the Cisco study, the top driver for communication
connectivity was data analytics, which enabled better
and more efficient decision making (Figure 3).
Predictive or proactive analytics can be leveraged in
the facility to better manage asset maintenance on plant
equipment, while data can be used to ensure equipment
is fixed or replaced based on its actual condition, rather
than on a preset timescale or use. Optimised
performance from real time feedback of equipment
parameters can be realised and deliver savings, even
through small efficiency improvements.
The ability to securely exchange information
between operational, enterprise, or external sources
automatically, depending on credentials, opens
opportunity for new business and support models.
Cisco is engaged on a number of customer
implementations using a combination of real time
streaming and historical analytics, edge-based
computing and processing, and cloud-based services.
This provides an end to end platform solution for data
gathering, local analytics and processing, secure
transport, comprehensive analytics, modelling (via
partners), and application integration for enhanced oil
recovery (EOR), and gas detection services. In some early
projects with oil and gas majors in Asia, predictions for
EOR are between 25 - 43%, over a five year period.
Security
Historically, a security by obscurity approach has been
taken for the process control domain. Security measures
were often based on the assumption that if the location
or access method of a vulnerable point is not widely
known, it will not be exploited.
As different technologies and use cases are adopted,
new and diverse devices are being connected to the
network. This brings with it a potentially wider set of
security attack challenges – intentional, unintentional,
external and internal.
In addition, information, resources and tools have
increased, making it easier for hackers to gain an
understanding of legacy and traditional protocols, and
to gain access to control systems.
As companies bring together OT and IT, and the
borders between these traditionally separate domains
blur, they must also align security strategies and work
more closely together to ensure end to end holistic
security (Figure 4). This includes architecture following
Figure 3.
Reasons for connectivity.
Figure 4.
Security span of influence.


